Every few years, infrastructure finds a new layer it didn't know it needed. This time, it's MCP — the Model Context Protocol.
You'll see it popping up everywhere: in Claude, Cursor, AWS AgentCore, and now Similarweb's MCP Server as a response to a deeper architectural gap. The old API model wasn't designed for environments where code makes its own decisions.
MCP introduces context into the protocol itself, turning integration from a one-time configuration into a governed relationship.
Read on to see:
- Why traditional API logic breaks in multi-agent environments
- How MCP embeds context and policy into every interaction
- What new security boundaries it creates for connector design
📚Related: Agentic AI ≠ Chatbot: What Changes in Your Backend
Why MCP Rewrites the Rules of Connection

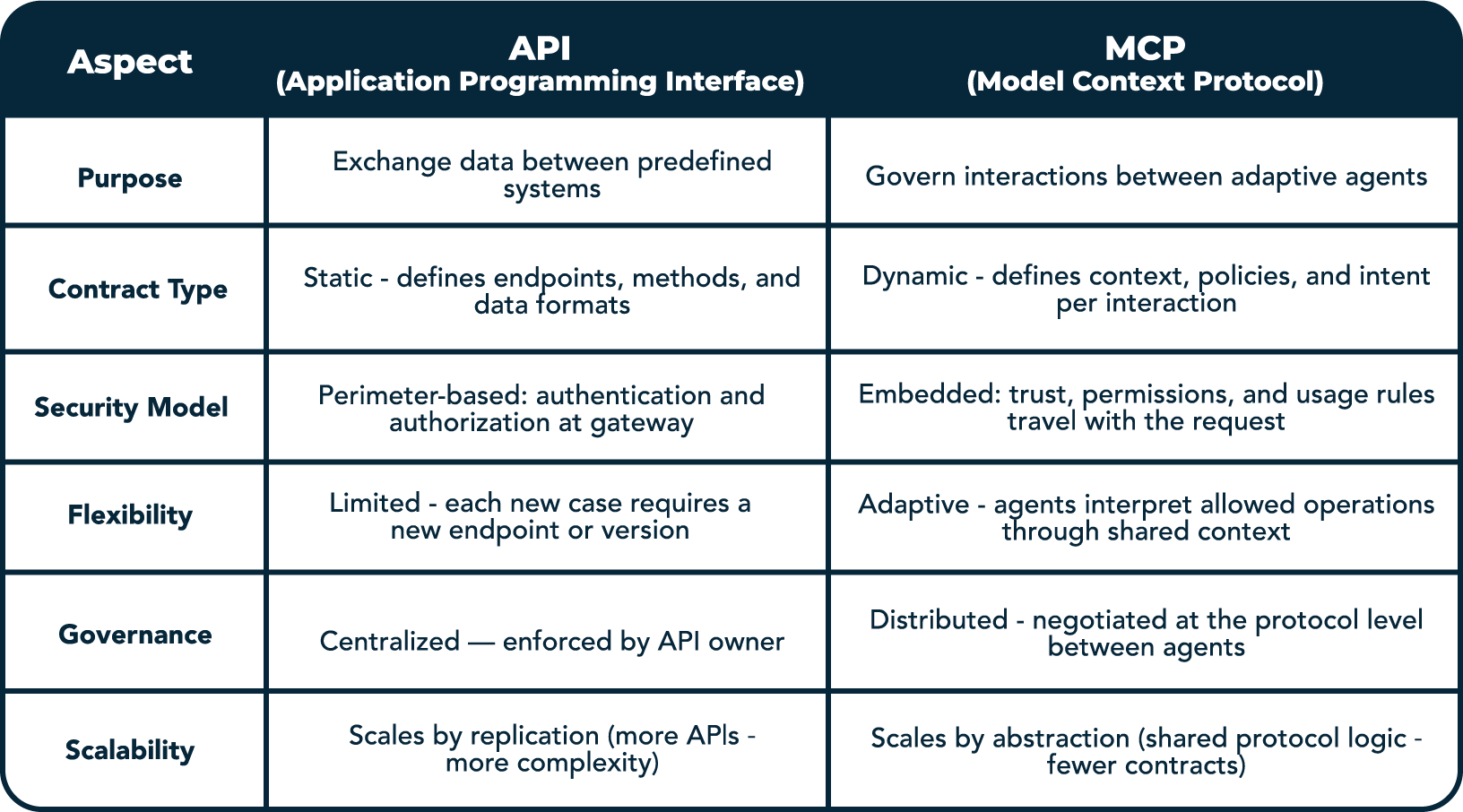
APIs were designed for predictable systems that exchanged fixed data through fixed rules.
They work as long as every request is known in advance and every response follows the same pattern.
But AI agents don't stay within those limits. They connect across domains, reuse data in new ways, and make calls no engineer planned for. Consequently, you get control at the expense of adaptability.
The Model Context Protocol (MCP) replaces static access rules with contextual ones. Instead of describing what data can be exchanged, MCP describes the conditions of that exchange:
- Who is calling?
- For what purpose?
- Under which constraints?
Each interaction carries its own definition of trust.

In a classic API, enforcement happens at the perimeter. In MCP, control moves into the protocol. Context travels with the request: metadata, intent, policy, and permissions form part of the same message. Systems negotiate how that communication is allowed to happen.
This design removes much of the hard-coded logic that usually ties integrations to a specific structure.
For example
Similarweb's MCP Server lets agents access its market data together with schema, rate limits, and compliance metadata. AWS AgentCore applies the same principle across organizations, where agents use MCP to exchange context about identity, access scope, and boundaries without manual configuration.
MCP changes the APIs' purpose. Where an API exposes data, MCP defines how that data can exist in a shared operational space. It shifts integration from static connectivity to managed interaction, an architectural adjustment that makes systems more interpretable and less brittle.
Why Security Fails When Systems Outgrow Their APIs
APIs have always lived between openness and control. Keys, tokens, and OAuth flows grant access once, and from that point, access remains fixed.
That model fails once systems start interacting beyond their predefined scope. Agents combine calls, reuse data, and cross organizational boundaries that no static rule can anticipate. A single key can authorize more than intended.
For instance, an agent renewing tokens across three organizations introduces a context no API key can capture. What starts as a convenience for integration often turns into an operational exposure.
- Security Debt of Traditional APIs
Most authorization still relies on perimeter logic. Once a request passes verification, it inherits privileges far broader than necessary. Least-privilege setups rarely survive production pressures. They're expensive to maintain, so engineers grant more than required. The result: excessive trust, weak traceability, and no reliable record of what actions were taken under that trust.
- Contextual Trust as a Design Principle
MCP defines access as a negotiation, not a fixed rule. Each request carries its own context: who acts, for what reason, and within what limits. Privileges exist only for the duration of that action. The agent operates within a defined boundary, without direct access to raw data. Control is expressed through the scope of context.
- Visibility Instead of Restriction
Traditional security reduces visibility to minimize risk. MCP keeps actions observable. Each request can log not just that something happened, but why. That auditability makes behavior explainable without over-engineering access rules. Instead of relying on restrictions, systems gain accountability through evidence.
- The Future Connector
In multi-tenant and cross-organization systems, static secrets stop scaling long before the workload does. Each connector must define and enforce its own trust boundary. MCP formalizes this principle: security becomes part of the protocol.

How MCP Turns Integration Into Infrastructure
- Coordination without fragmentation
MCP removes manual rules like "if X can access Y." Permissions become part of the protocol. It cuts down inter-team dependencies and eliminates the need to sync hundreds of keys, tokens, and roles. Integrations scale without a central "access manager".
- Controlled behavior
In classic APIs, trust is defined by code. In MCP, it's defined by context. An agent can act only within the scope of its current task, the protocol limits what actions, data, and duration are valid. This shifts control from enforcement to architecture: risk reduction comes from design, not from adding more restrictions.
- Security without friction
Security teams don't need to interrupt development. All agent actions are logged inside the protocol itself, showing not only what happened, but why. That means risk review happens through visibility: security becomes traceable without blocking the delivery cycle.
- Scalable trust across organizations
MCP moves trust boundaries from static API rules to contextual requests. As more agents and partner systems appear, there's no need to rebuild access policies: each interaction carries its own constraints. Trust scales automatically, without manual oversight, policy duplication, or loss of accountability.
📚 Related: Accelerating AI-Powered Development Without Losing Control
Architectural Implication
MCP shifts integration from code to coordination.
In traditional systems, you connect APIs, test permissions, and hope nothing breaks when policies change. With MCP, those boundaries live inside the protocol itself: systems describe what they share and under what logic they expose.
Control moves from the network edge to the interaction level. For large infrastructures, it means fewer hidden dependencies and less manual oversight. Trust stops being a one-time setup and becomes an operational property: visible, testable, and easy to reason about.
The Governance Layer AI Was Missing
MCP marks a power shift in how digital systems cooperate. It moves decision-making from network edges to the protocol itself, where context, scope, and access are negotiated in real time.
Cloud vendors get predictable governance across tenants. Enterprises gain traceable integrations that don't depend on static security gates. Security teams finally see what automation actually does, not just whether it's authorized.
APIs connected systems. MCP coordinates them. That's the missing governance layer: not invented, but discovered through necessity.